A new report from the Deloitte Center for Government Insights - a division of the management consultancy focused on governmental risk - highlighted a link between high ransom payments in cases of government hacking and more costly demands from perpetrators

Data suggests that higher ransom payments could be driving increases in government hacking (Credit: U.S.Air Force Graphic by Adam Butterick)
Cyber insurance may “unintentionally” be encouraging hacking of government organisations because claims are resulting in increasingly high ransom payments, according to a new report.
The document, released by the Deloitte Center for Government Insights, said cyber insurance was an enabling factor that encouraged hackers to ask for more money.
It highlighted that drawing a causative relationship between higher ransom demands and higher payments is a “chicken and egg” situation, but said there’s a “clear correlation” between the ransoms paid and the volume of attacks.
Deloitte’s report said: “When attacked, no organisation wants to be helpless, but those that use cyber insurance policies to cover ransom payments may unintentionally be fueling the increase in ransomware attacks.
“Cyber insurance, poor defence, and the criticality of government services are creating a positive feedback loop where attackers are asking for and getting more money more often.”
Ransomware attacks on US government organisations yielded 10 times the average amount of ransom collected from the country’s commercial entities in the second half of 2019, according to a study by analytics and response service provider Coveware.
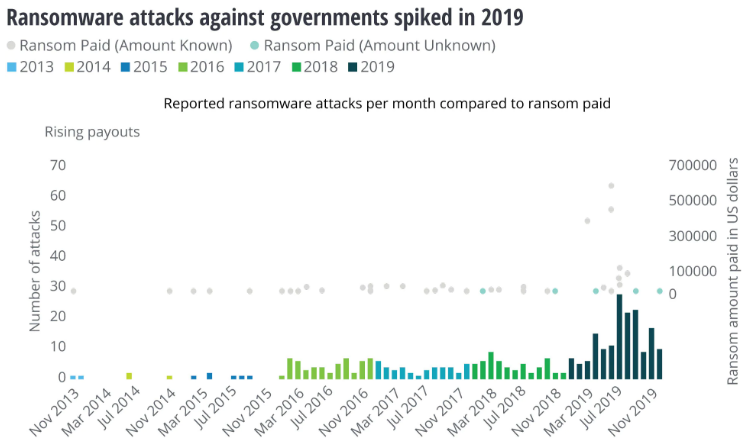
Deloitte released its analytics to show the correlation between higher payments and more attacks.
“While paying the ransom in a ransomware attack may seem to be an easy, short-term solution – in the long run, it may make the problem worse, encouraging attackers to continue to target governments,” the report added.
Attacks on government have increased alongside cyber insurance growth
Deloitte’s report examined the question of why, when ransomware has been around for decades and government agencies haven’t dramatically updated their IT security or legacy systems, is the public sector such a gold mine for hackers.
“Certainly, the recent increase in cyber insurance plays some role,” it said.
But it added it can’t be the only factor, as the majority of policies in the sector are bought by commercial businesses, not the public sector.
For Deloitte, this is where the other two factors, poor defence and the critical nature of government services come into play.
“This appears to create a situation where, aided by cyber insurance, more vulnerable government organisations are paying more than better-protected ones,” it added.
Describing the situation as “like blood in the water”, Deloitte believes this specific mix of factors attracted one particular criminal syndicate in Russia, which it claims created the “Ryuk” strain of ransomware commonly attributed to state and local government hacking in the US.
How have ransomware threat actors changed their approach in recent times?
Technology-focused news site Computer Business Review has reported extensively on ransomware attacks in the US and observed the changes in ransomware hacking over the years.
The website’s editor Ed Targett said: “Ransomware attacks are getting significantly more effective.
“This is primarily because those behind them are dropping early ‘spray-and-pray’ approaches in favour of much more customised attacks on carefully chosen targets.”
He said this includes techniques such as using previously compromised email accounts to launch phishing campaigns, a technique that allows hackers to access systems and assess their vulnerabilities before deploying a ransomware payload.
“Attackers will use compromised emails from contacts who have been in recent correspondence with the recipient; the subject lines often mirror the most recent email exchange,” said Targett.
“It’s a clever technique and when it succeeds, attackers now often spend significant amounts of time ‘living off the land’ and conducting systems reconnaissance before triggering the ransomware.”
Despite painting a bleak picture, there are steps Targett advises any organisation worried about ransomware to take.
“Resilience is key here. The main thing to do is back-up religiously and store your back-ups outside your network, as even USB drives or cloud storage can be vulnerable.
“It’s also important to improve security hygiene by patching regularly, segmenting networks, and crucially, introducing multi-factor authentication.”
